 |
Crypt-o system options - Multi-factor authentication |



|
You can enable Multi-factor authentication (MFA) to additionally secure user accounts in Crypt-o. Use this page to configure MFA.
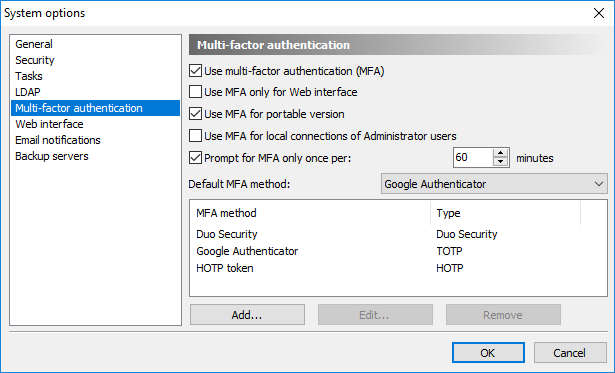
Configuration of Multi-factor authentication
Crypt-o supports the following MFA types:
| • | TOTP - Time-based One-Time Password algorithm; |
| • | HOTP - HMAC-based One-Time Password algorithm; |
| • | Duo Security. |
The following options are available:
![]() Use multi-factor authentication (MFA) - to start using MFA select this option.
Use multi-factor authentication (MFA) - to start using MFA select this option.
![]() Use MFA only for Web interface - when this option is selected MFA will be used only when connecting Crypt-o Server via the Web interface. When running Crypt-o Client application, MFA will not be used.
Use MFA only for Web interface - when this option is selected MFA will be used only when connecting Crypt-o Server via the Web interface. When running Crypt-o Client application, MFA will not be used.
![]() Use MFA for portable version - when this option is selected MFA will be also used when running a portable/offline version of Crypt-o.
Use MFA for portable version - when this option is selected MFA will be also used when running a portable/offline version of Crypt-o.
![]() Use MFA for local connections of Administrator users - when this option is selected MFA will be also used when a user with the System administrator permission connects to Crypt-o Server using the localhost/loopback interface. This option is not selected by default to allow System administrators to bypass MFA using a local server connection if something went wrong.
Use MFA for local connections of Administrator users - when this option is selected MFA will be also used when a user with the System administrator permission connects to Crypt-o Server using the localhost/loopback interface. This option is not selected by default to allow System administrators to bypass MFA using a local server connection if something went wrong.
![]() Prompt for MFA only once per - when this option is selected, Crypt-o will prompt a user to perform MFA only once per the specified time interval.
Prompt for MFA only once per - when this option is selected, Crypt-o will prompt a user to perform MFA only once per the specified time interval.
Default MFA method - use this option to select what MFA method will be used by default for all user accounts. If needed you can set an MFA method individually for each user account.
All configured MFA methods are displayed in the list.
Press the Add... button to add a new MFA method.
To edit an MFA method select it in the list and press Edit...
To delete an MFA method select it in the list and press Remove.
![]() NOTE: If you lost administrator access to Crypt-o due to inability to pass the MFA, you can restore access using the following method:
NOTE: If you lost administrator access to Crypt-o due to inability to pass the MFA, you can restore access using the following method:
- Use a text editor to open the server.ini file in the data folder of Crypt-o Server.
- Find the UseMFALocalAdmin parameter in the [Options] section and delete it if it exists.
- Save the changes to server.ini.
- Restart the Crypt-o Server service.
- Run Crypt-o Client on the computer where Crypt-o Server is running.
- Click Options... on the logon prompt.
- Type localhost as the Crypt-o Server parameter.
- Press OK and log on as a user with the System administrator permission.
TOTP
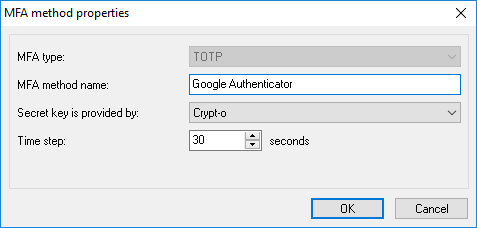
TOTP method properties
Time-based One-Time Password algorithm (TOTP) is widely used for Multi-factor authentication. TOTP codes can be generated by a specialized device (token) or by an application running on your phone or tablet.One of the popular free OTP applications is Google Authenticator.
The following TOTP options are available:
MFA type - set it to TOTP.
MFA method name - set a user-friendly display name of this authentication method. It is recommended to use a real device/token name, since it will be presented to users of Crypt-o during MFA processing.
Secret key is provided by - choose which party provides a secret key. This depends of an authentication device you are going to use.
Crypt-o - if this option is selected, Crypt-o will generate a secret key during enrollment of new MFA user. The secret code (in form of a QR-code or text) must be passed to the authentication device to complete the enrollment. Use this option if you are going to use an OTP application such as Google Authenticator.
Authentication device - if this option is selected, Crypt-o will request the device's secret key during enrollment of new MFA user. Usually OTP tokens contain pre-generated keys - choose this option in such case.
Crypt-o or Authentication device - if this option is selected, Crypt-o will allow to choose which party provides the secret key during enrollment of new MFA user.
Time step - a time interval to generate distinct TOTP codes. 30 seconds is the default value for most TOTP implementations.
HOTP
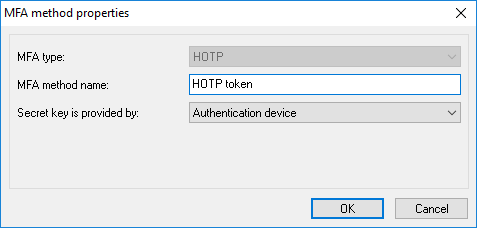
HOTP method properties
HMAC-based One-Time Password algorithm (HOTP) is widely used for Multi-factor authentication. HOTP codes can be generated by a specialized device (token) or by an application running on your phone or tablet.One of the popular free OTP applications is Google Authenticator.
The following HOTP options are available:
MFA type - set it to HOTP.
MFA method name - set a user-friendly display name of this authentication method. It is recommended to use a real device/token name, since it will be presented to users of Crypt-o during MFA processing.
Secret key is provided by - choose which party provides a secret key. This depends of an authentication device you are going to use.
Crypt-o - if this option is selected, Crypt-o will generate a secret key during enrollment of new MFA user. The secret code (in form of a QR-code or text) must be passed to the authentication device to complete the enrollment. Use this option if you are going to use an OTP application such as Google Authenticator.
Authentication device - if this option is selected, Crypt-o will request the device's secret key during enrollment of new MFA user. Usually OTP tokens contain pre-generated keys - choose this option in such case.
Crypt-o or Authentication device - if this option is selected, Crypt-o will allow to choose which party provides the secret key during enrollment of new MFA user.
Duo Security
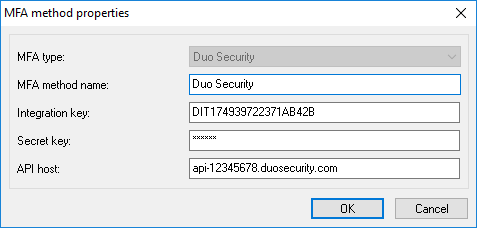
Duo Security method properties
Duo Security is a popular provider of Multi-factor authentication.
In order to use the Duo Security method in Crypt-o, you need:
| • | Log in to the Duo Admin Panel and navigate to Applications. |
| • | Click Protect an Application and locate Auth API or Web SDK in the applications list. Click Protect this Application to get your Integration key, Secret key, and API host. |
The following options are available for Duo Security:
MFA type - set it to Duo Security.
MFA method name - set a user-friendly display name of this authentication method.
Integration key - copy the integration key from the Application page in the Duo Admin Panel.
Secret key - copy the secret key from the Application page in the Duo Admin Panel.
API host - copy the API host name from the Application page in the Duo Admin Panel.

